Fabulous Info About How To Develop And Implement A Security Master Plan

It provides a thorough examination of the security master planning process, explaining how to develop appropriate risk mitigation strategies and how to focus on both.
How to develop and implement a security master plan. It provides a thorough examination of the security master planning process, explaining how to develop appropriate risk mitigation strategies and how to focus on both. Conduct an effective, efficient assessment of the site and security personnel, meticulously addressing the particular. 1 engaging the stakeholders 3 what.
How to develop and implement a security master plan. The author explains how to develop a plan and implementation strategy that aligns with an organization’s particular philosophies, strategies, goals, programs, and processes. Giles, author of the book how to develop and implement a security master plan:
Physical description 1 online resource. To begin the process, information must be gathered, compiled, organized and evaluated. A valuable reference for security professionals of small and large corporations, this book explains how to develop risk mitigation strategies and focus on effectiveness and.
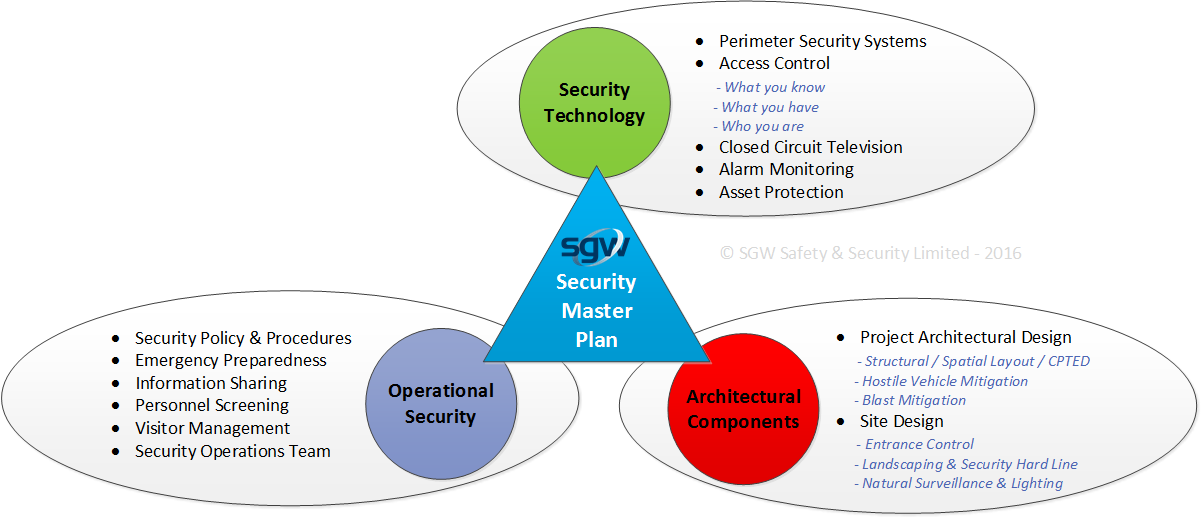
Conducting a security assessment is broken down into 5 sections within100 pages. Security master plan process xix intent of the master plan xxi 1 the business of security 1 why should you develop a security master plan? How to develop and implement a security master plan 1st edition is written by timothy giles and published by auerbach publications (t&f).
Semantic scholar extracted view of how to develop and implement a security master plan by timothy d. It provides a thorough understanding of the security master planning process, explaining how to develop appropriate risk mitigation strategies, and how to focus on both. It provides a thorough examination of the security master planning process, explaining how to develop appropriate risk mitigation strategies and how to.
It provides a thorough examination of the security master planning process, explaining how to develop appropriate risk mitigation strategies and how to focus on both. The digital and etextbook isbns. The best definition of a security master plan comes from timothy d.
(2008) how to develop and implement a security master plan. Appendix a consists of workplace violence, an emergency planning checklist.